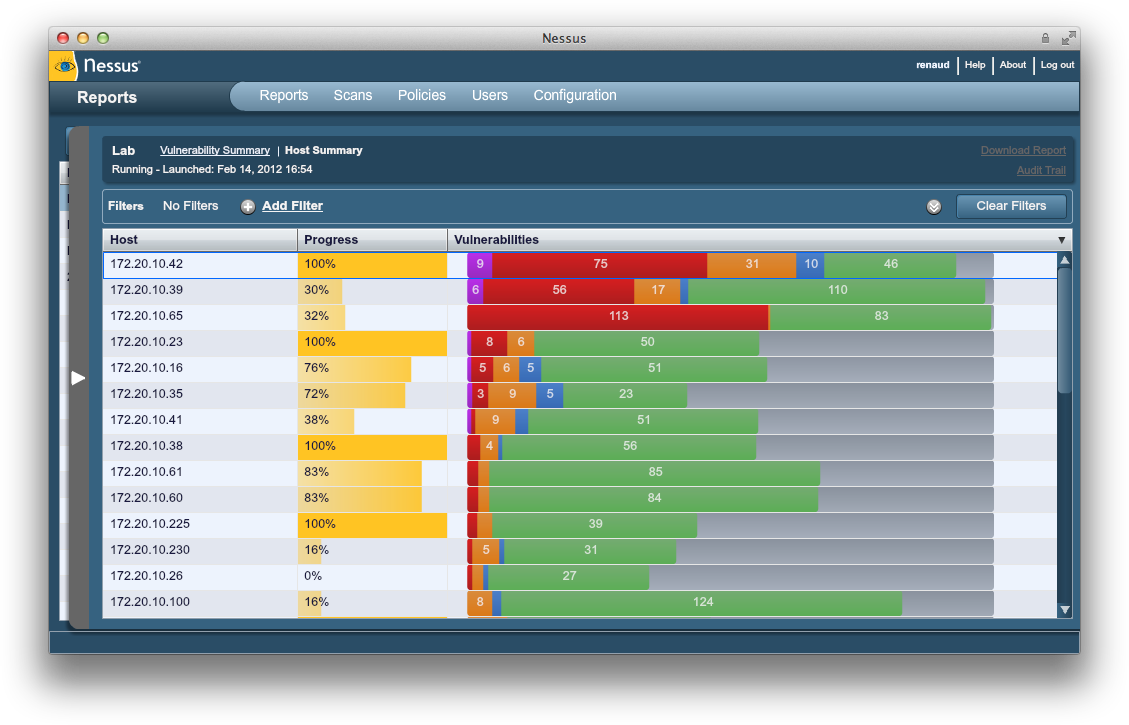
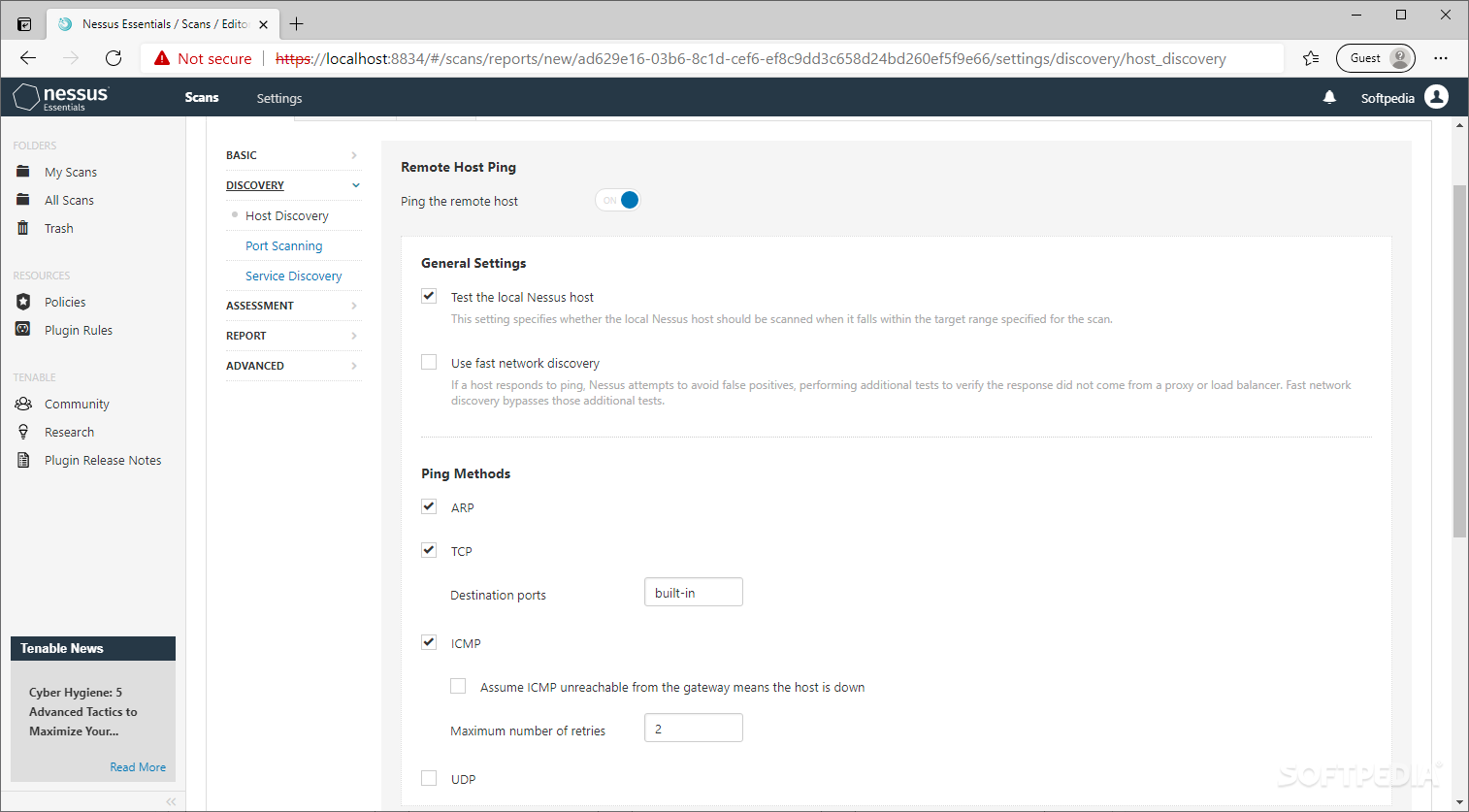
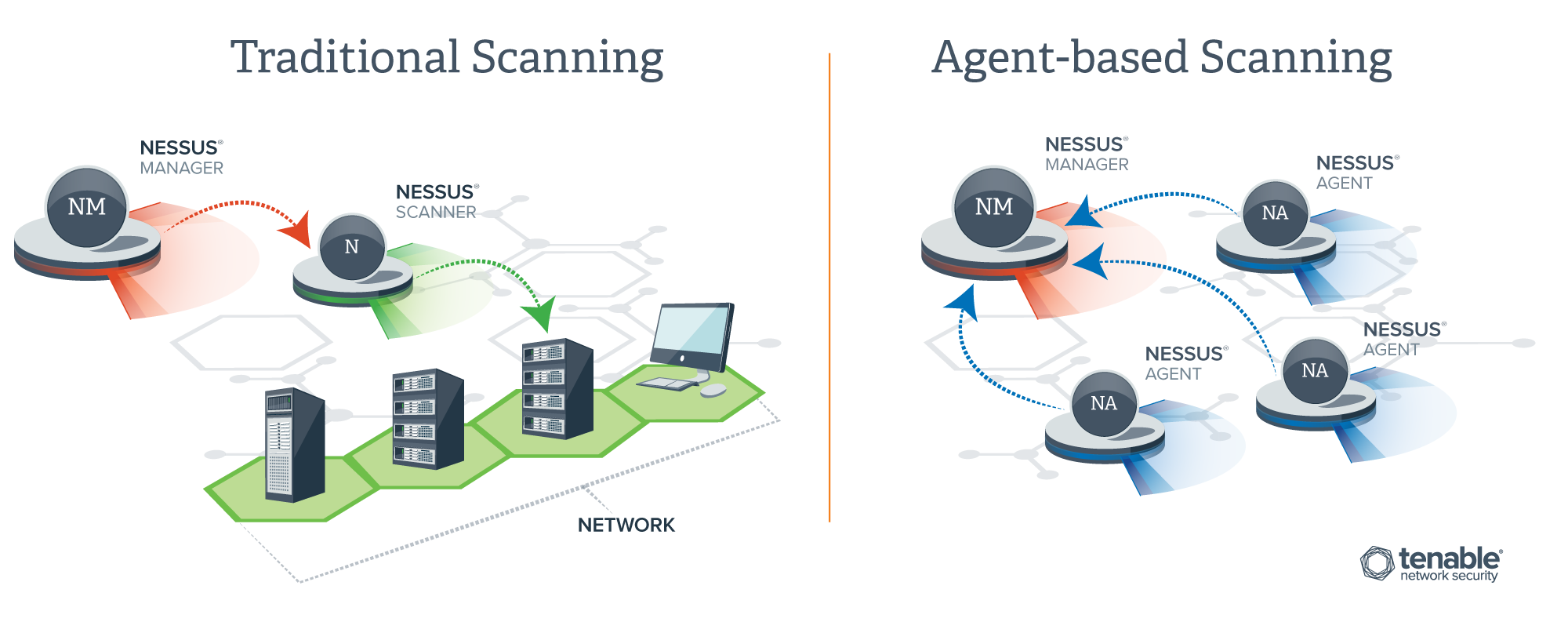
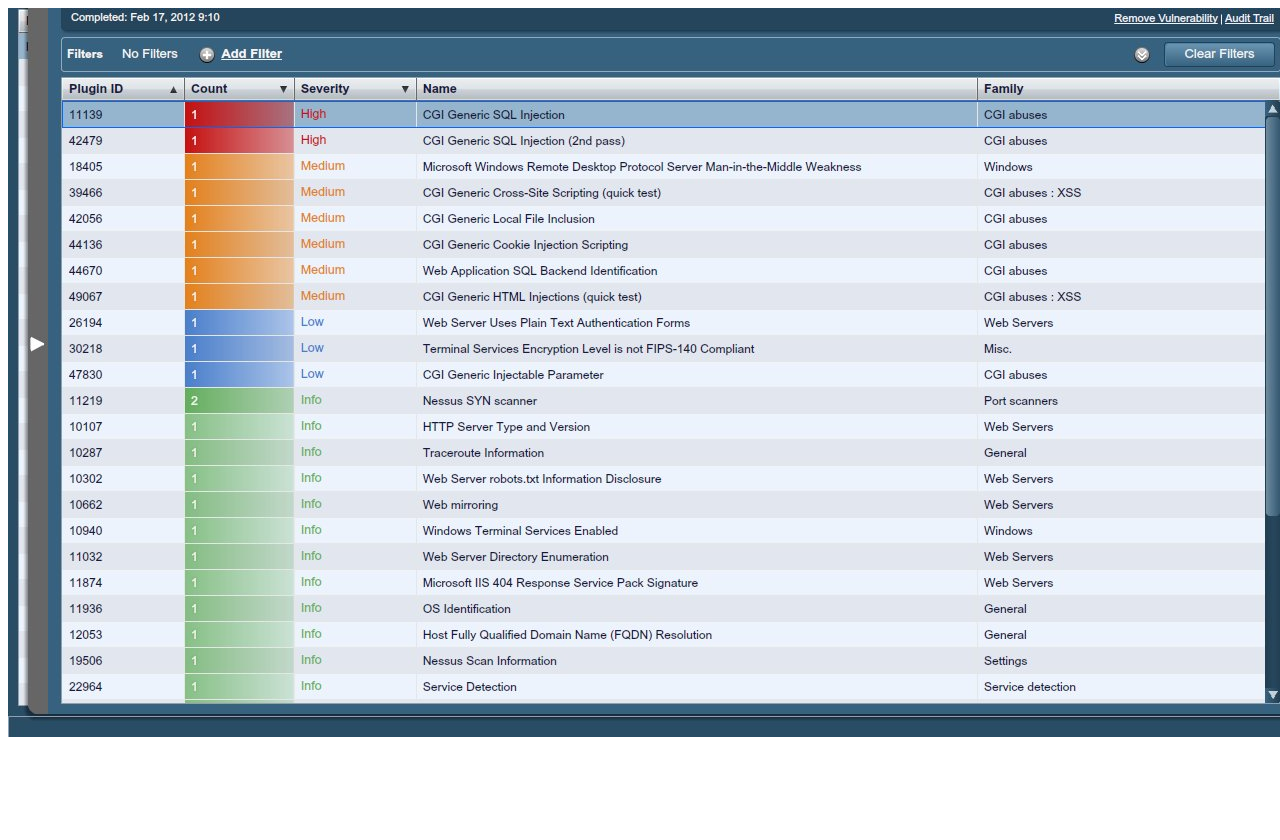
Nessus, Snort, Ethereal Power Tools: Customizing Open Source Security Applications (Jay Beale's Open Source Security Series) [Neil Archibald, Gilbert Ramirez, Noam Rathaus, Josh Burke, Brian Caswell, Renaud Deraison on Amazon. FREE shipping on qualifying offers. This book will cover customizing Snort to perform intrusion detection and prevention; Nessus to analyze the. NESSUS is a modular computer software program for performing probabilistic analysis of structuralmechanical components and systems. KEYWORDS We have only been studying the Centaurean bodies, and those out past Pluto, for a short while, so any keywords we use are tentative, and may change as we learn more about them. It was like the minute I saw that picture, I was thinking then my eyes fell to the words. NESSUS OMG My very sexy landlord, hair dresser was also a very talented artist, he had a painting of this scene, along with Heracles, little different, but I recognized it and the story immediately. Dans la mythologie grecque, Nessos ou Nessus (en grec ancien Nessos, en latin Nessus) est un centaure, issu comme la plupart de ses congnres de l'union d'Ixion et Nphl Binary download files for Nessus Professional, Nessus Manager, and connecting Nessus Scanners to Tenable. Nessus is deployed by millions of users worldwide to identify vulnerabilities, policyviolating configurations and malware that attackers use to penetrate your or your customer's network. Nessus is known for his role in the story of the Tunic of Nessus. After carrying Deianeira, the wife of Heracles, across the river, he attempted to force himself upon her. Heracles saw this from across the river and shot a Hydrapoisoned arrow into Nessus's breast. La Lune cuivre, en astronomie, est un phnomne optique de diffusion et de dispersion de la lumire qui se produit durant les clipses de Lune. La Lune prend une apparence cuivre (parfois qualife tort de rousse) chaque fois qu'elle est basse sur l'horizon, car la lumire du Soleil qui l'claire est filtre en passant au travers de l'atmosphre terrestre. To the left of the map marker for Nessus Treasure Map# 1 is an underground cave. Go through it and it will lead you to a cavern with a portal. The Nine Hells of Baator, sometimes Hell or Hells, also known as Baator in Infernal, was the home of the devils. It was a plane of sinister evil and institutional cruelty organized in a strict caste system with a very rigid chain of command. Unlike the demons of the Abyss, the devils were highly Symantec helps consumers and organizations secure and manage their informationdriven world. Our software and services protect against more risks at more points, more completely and efficiently, enabling confidence wherever information is used or stored. The Symantec Connect community allows customers and users of Symantec to network and learn more about creative and innovative ways to. A centaur, who carried Deianeira across the river Evenus, but, wishing to run away with her, ie was slot by Heracles with a poisoned arrow, which afterwards became the cause of Heracles' own death. Nessus of Nes(s)os was in de Griekse mythologie een centaur, zoon van Ixion en Nephele. Hij had de overzetdienst bij de rivier Evenus. Hij droeg Deianira over de stroom, terwijl haar echtgenoot Heracles te voet overstak. Toen Nessus zich aan haar wilde vergrijpen, riep zij Heracles om hulp, die hem met een gifpijl neerschoot. Source Nessus is a large centaur, who is known as the River Guardian. He is a minor villain in the film Hercules. Megara was sent by Hades to recruit Nessus for his army. In exchange for his service, Nessus wanted Meg to be his lover. Meg's refusal only made Nessus. Nessus identifies the vulnerabilities, configuration issues and malware that hackers could use to penetrate your network. Nessus is a proprietary vulnerability scanner developed by Tenable Network Security. It is free of charge for personal use in a nonenterprise environment. According to surveys done in 2009 by sectools. org, Nessus is the world's most popular vulnerability scanner, taking first place in the 2000, 2003, and 2006 security tools survey. Tenable Network Security estimated in 2005 that it was used by. com will teach you the way to harness the dark forces. The Updated Version of the Bestselling Nessus Book. This is the ONLY Book to Read if You Run Nessus Across the Enterprise Ever since its beginnings in early 1998, the Nessus Project has attracted security researchers from all walks of life. Linux Internet Server Security and Configuration Tutorial. Security configuration and setup for Linux servers exposed to the internet: Any computer connected to the internet will require steps and precautions to be taken to reduce the exposure to hacker threats. Windows.